Overview
In this configuration, you can use the same API, CLI, and web interface that PlanetScale offers, with the benefit of running entirely in a GCP project that you own and PlanetScale manages for you.Architecture
As you can see in the architecture diagram below, the PlanetScale data plane is deployed inside of a PlanetScale-controlled project in your GCP organization. The Vitess cluster will run within this project, orchestrated by Kubernetes. We distribute components of the cluster across three GCP zones within a region to ensure high availability. You can deploy PlanetScale Managed to any GCP region with at least three zones, including zones not supported by the PlanetScale self-serve product, so long as the region supports the required GCP services (including but not limited to Google Compute Engine (GCE), Google Kubernetes Engine (GKE), Cloud Storage, Persistent Disk, Cloud Key Management Service (Cloud KMS), Cloud Logging). Backups, part of the data plane, are stored in Cloud Storage inside the same project. PlanetScale Managed uses isolated GCE instances as part of the deployment.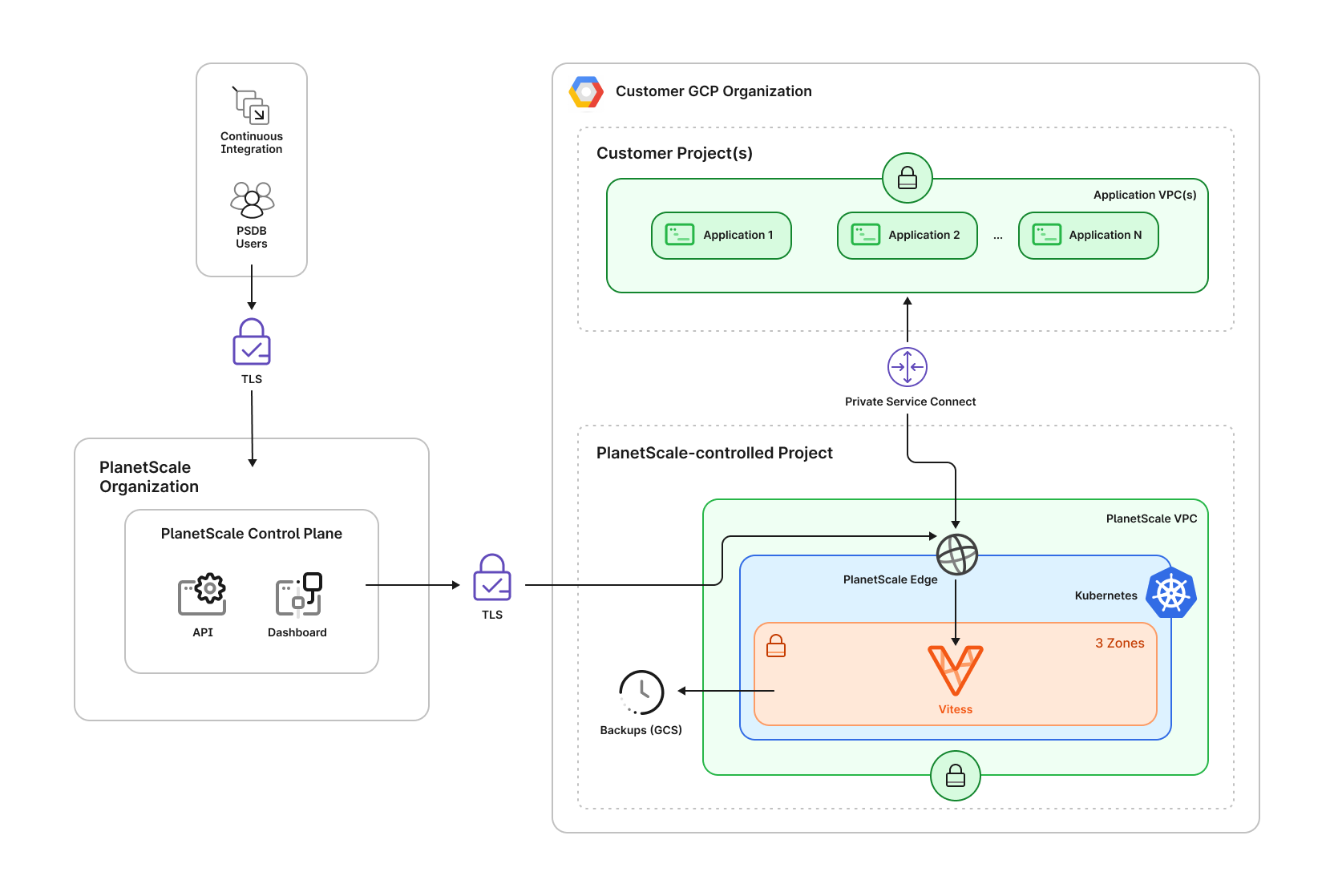
app.planetscale.com.
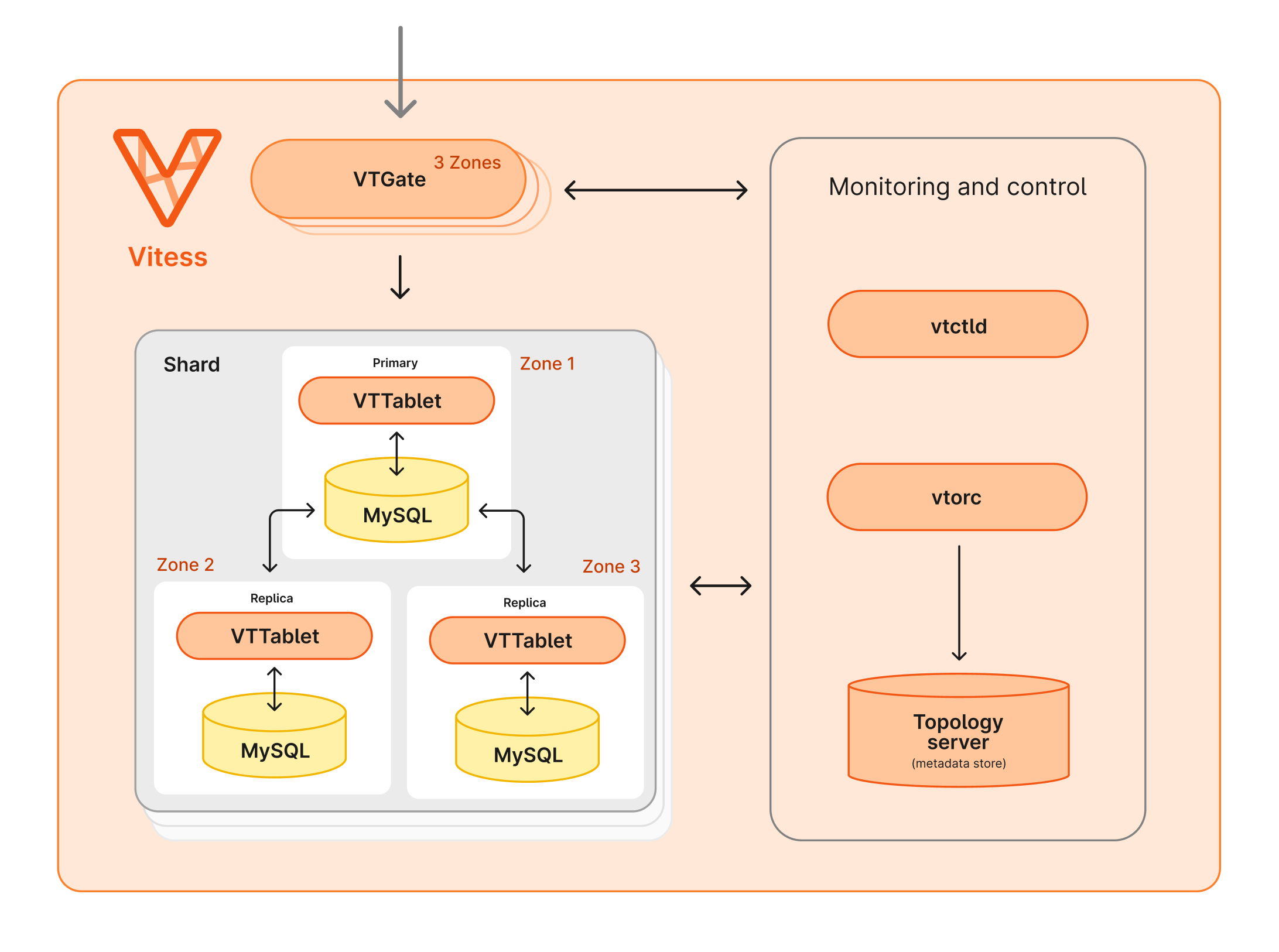
The Vitess cluster running inside Kubernetes is composed of a number of Vitess Components.
All incoming queries are received by one of the VTGates, which then routes them to the appropriate VTTablet.
The VTGates, VTTablets, and MySQL instances are distributed across 3 availability zones.
Security and compliance
PlanetScale Managed is an excellent option for organizations with specific security and compliance requirements. You own the GCP organization and project that PlanetScale is deployed within an isolated architecture. This differs from when your PlanetScale database is deployed within our GCP organizations. Along with System and Organization Controls (SOC) 2 Type 2 and PlanetScale security and compliance practices that PlanetScale has been issued and follows, we can also sign BAAs for HIPAA compliance on PlanetScale Managed.PlanetScale manages the entire project and can NOT support customers running Terraform or other configuration management in the project.
GCP Private Service Connect
By default, all connections are encrypted, but public. Optionally, you also have the option to use private database connectivity through GCP Private Service Connect, which is only available on single-tenancy deployment options, including PlanetScale Managed.If you have any questions or concerns related to the security and compliance of PlanetScale Managed, please contact us, and we will be happy to discuss them further.

