Overview
In this configuration, you can use the same API, CLI, and web interface that PlanetScale offers, with the benefit of running entirely in an AWS Organizations member account that you own and PlanetScale manages for you.Architecture
The PlanetScale data plane is deployed inside of a PlanetScale-controlled AWS Organizations member account in your AWS organization. The Vitess cluster will run within this member account, orchestrated via Kubernetes. We distribute components of the cluster across three AWS availability zones within your selected region to ensure high availability. You can deploy PlanetScale Managed to any AWS region with at least three availability zones, including those not supported by the PlanetScale self-serve product. Backups, part of the data plane, are stored in S3 inside the same member account. PlanetScale Managed uses isolated Amazon Elastic Compute Cloud (Amazon EC2) instances as part of the deployment.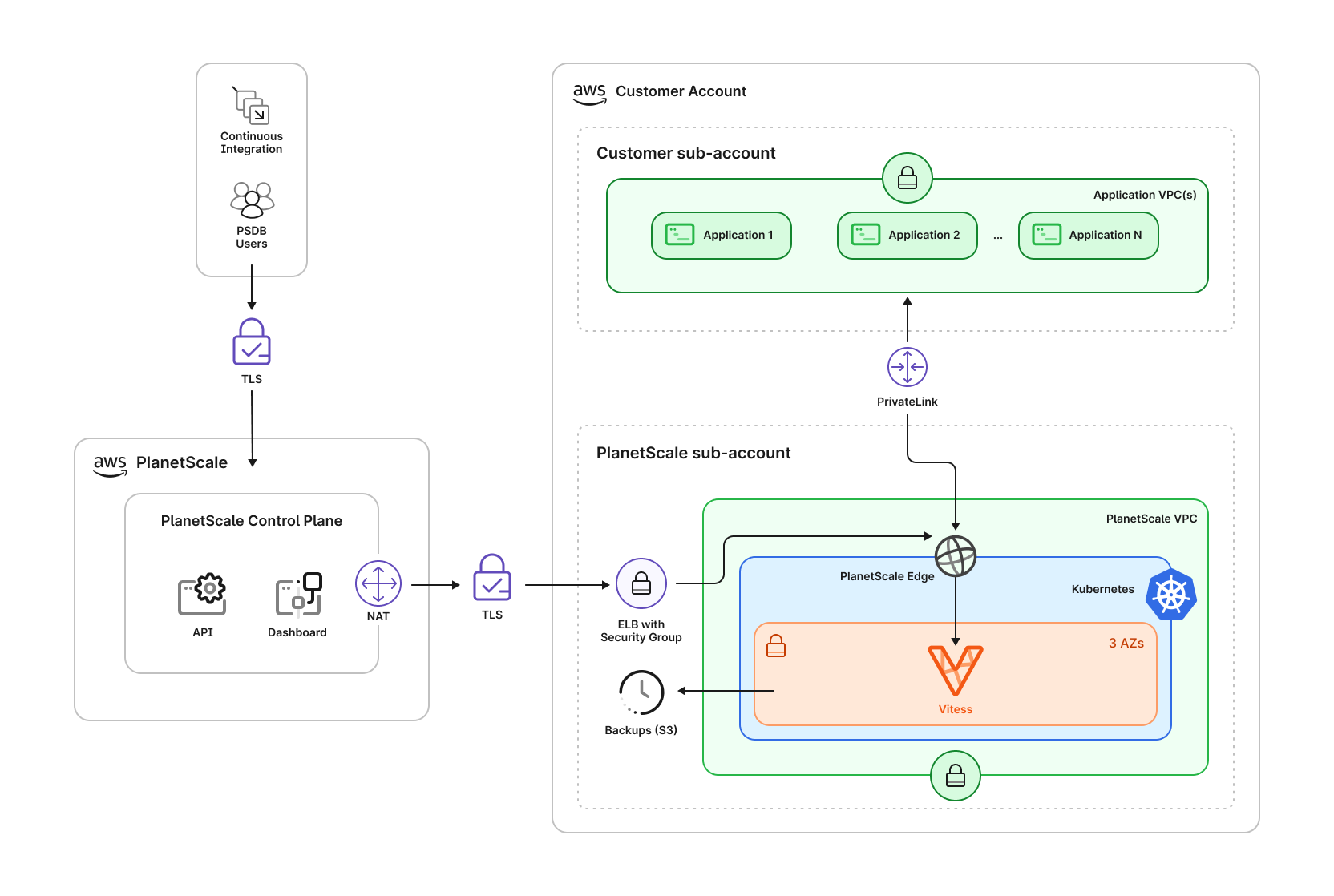
app.planetscale.com.
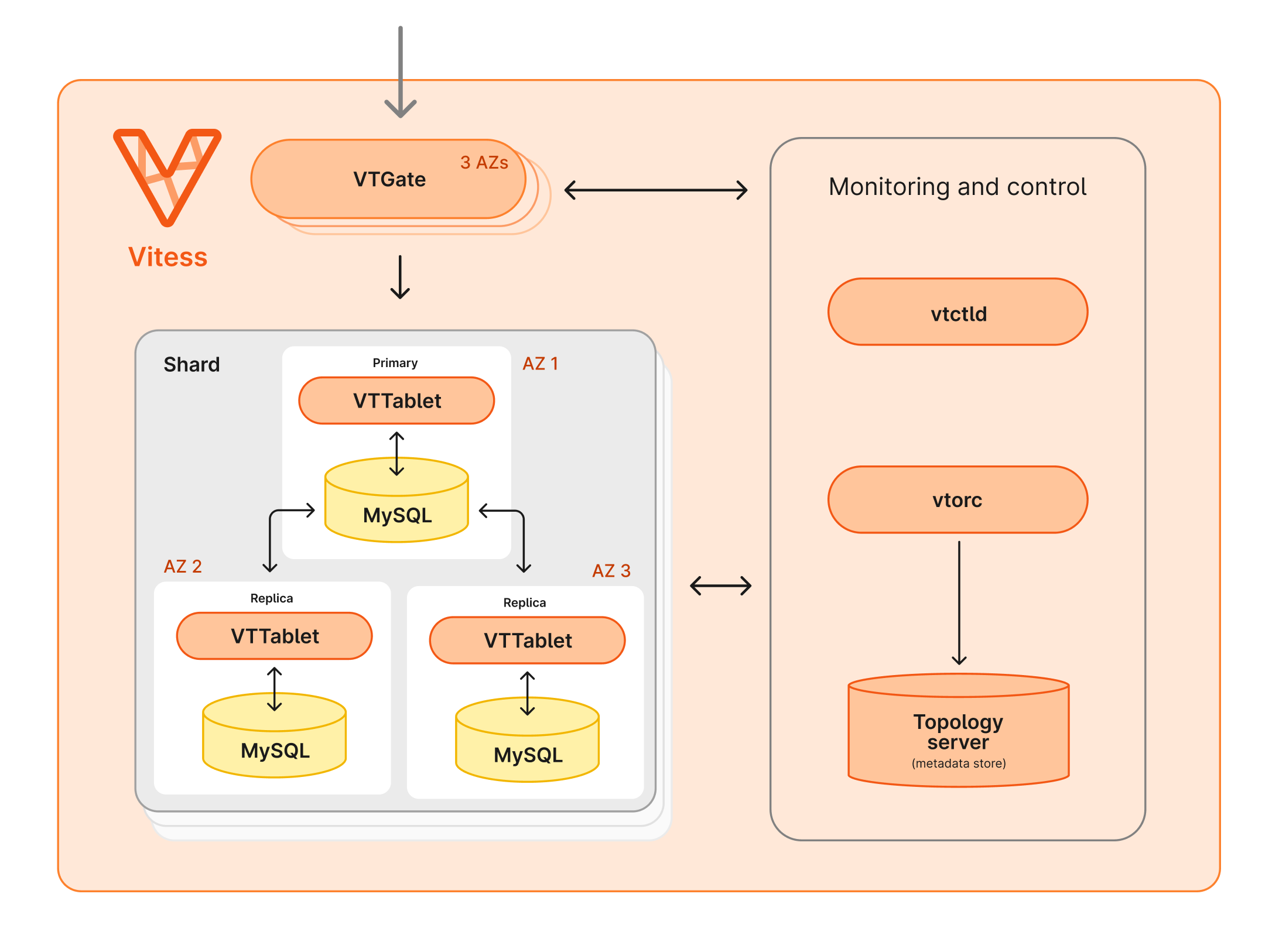
The Vitess cluster running inside Kubernetes is composed of a number of Vitess Components.
All incoming queries are received by one of the VTGates, which then routes them to the appropriate VTTablet.
The VTGates, VTTablets, and MySQL instances are distributed across 3 availability zones.
Security and compliance
PlanetScale Managed is an excellent option for organizations with specific security and compliance requirements. You own the AWS organization and member account that PlanetScale is deployed within an isolated architecture. This differs from when your PlanetScale database is deployed within our AWS organizations.PlanetScale manages the entire member account and can NOT support customers running Terraform or other configuration management in the member account.
PCI compliance
Along with System and Organization Controls (SOC) 2 Type 2 and other security and compliance practices that PlanetScale has been issued and follows, PlanetScale Managed has been issued an Attestation of Compliance (AoC) and Report on Compliance (RoC), certifying our compliance with the PCI DSS 4.0 as a Level 1 Service Provider. This enables PlanetScale Managed to be used via a shared responsibility model across merchants, acquirers, issuers, and other roles in storing and processing cardholder data.If you have any questions or concerns related to the security and compliance of PlanetScale Managed, please contact us, and we will be happy to discuss them further.
AWS PrivateLink
By default, all connections are encrypted, but public. Optionally, you also have the option to use private database connectivity through AWS PrivateLink.Fully private network isolation
You can also turn off public database access with a dual AWS PrivateLink setup. PlanetScale’s control plane will talk to your member account over AWS PrivateLink, and your VPCs will also communicate with your database over AWS PrivateLink. Please get in touch with your PlanetScale Account Manager for more information on how to set up fully private network isolation.Third-account customer-controlled public key infrastructure
PlanetScale Managed on AWS supports public key infrastructure (PKI) services. PlanetScale Managed customers can provide PlanetScale the use of a set of customer-managed keys in a third AWS account inside your organization. This third account is controlled by you, the customer. PlanetScale has no administrative access. Your organization is the custodian for this key material. PlanetScale uses the customer-managed keys to encrypt EBS volumes, S3 buckets, and for envelope encryption of backups.Billing
With any of the PlanetScale Enterprise offerings, including PlanetScale Managed, you have the option to purchase PlanetScale through the AWS Marketplace. In addition to this, the resources you use on PlanetScale will qualify against your EDP commitment.If you have any billing-related questions for PlanetScale Managed, please contact us, and we will be happy to discuss them further.

