Private connectivity - GCP Private Service Connect
(Updated )
Connecting to PlanetScale for Postgres privately via GCP Private Service Connect
GCP Private Service Connect is a highly available, scalable technology that enables you to privately connect your VPC to supported GCP services, endpoint services, and partner services. When you use GCP Private Service Connect, your network traffic between your VPC and PlanetScale stays within the Google Cloud network, without traversing the public internet.
When to use GCP Private Service Connect
By default, PlanetScale for Postgres databases use secure connections over the public internet with industry-standard TLS encryption. This approach is secure and meets the needs of most customers. However, you may want to consider GCP Private Service Connect if:
- Compliance requirements: Your organization has regulatory or compliance mandates that require database connections to avoid the public internet entirely
- Enhanced security posture: You want an additional layer of network isolation for sensitive data workloads
- Network architecture: Your existing GCP infrastructure is designed around private connectivity patterns
- Reduced network latency: GCP Private Service Connect can help reduce latency by keeping traffic within Google's network backbone
GCP Private Service Connect provides these security and compliance benefits by ensuring your database traffic never leaves the Google Cloud network.
Note
Normal PlanetScale for Postgres connectivity (as described in our standard connection documentation) uses secure TLS encryption over the public internet and is appropriate for most use cases. GCP Private Service Connect is primarily beneficial for compliance and enhanced security requirements.
Private Service Connect pricing
PlanetScale does not charge any additional fees for GCP Private Service Connect connectivity. However, Google Cloud charges standard Private Service Connect pricing for endpoints, which includes:
- Private Service Connect endpoint charges: Based on your endpoint configuration and usage
- Network egress charges: Standard GCP egress pricing may apply for data transfer
For current pricing in your region, see the GCP Private Service Connect pricing page.
Prerequisites
- A PlanetScale for Postgres database in a GCP region
- A GCP VPC in the same region where you want to establish the private connection
- Appropriate GCP IAM permissions to create Private Service Connect endpoints
- Required APIs enabled: Cloud DNS API and Service Directory API must be enabled in your project for automatic DNS zone creation (see GCP documentation)
Establishing a Private Service Connect endpoint
Retrieve the Private Service Name:
- From the PlanetScale organization dashboard, select the desired database
- Navigate to Settings from the menu on the left
- Select Roles
- Click on a role with permissions to the relevant
Branch - Copy the
Private HostandPrivate Service Namefrom the role details
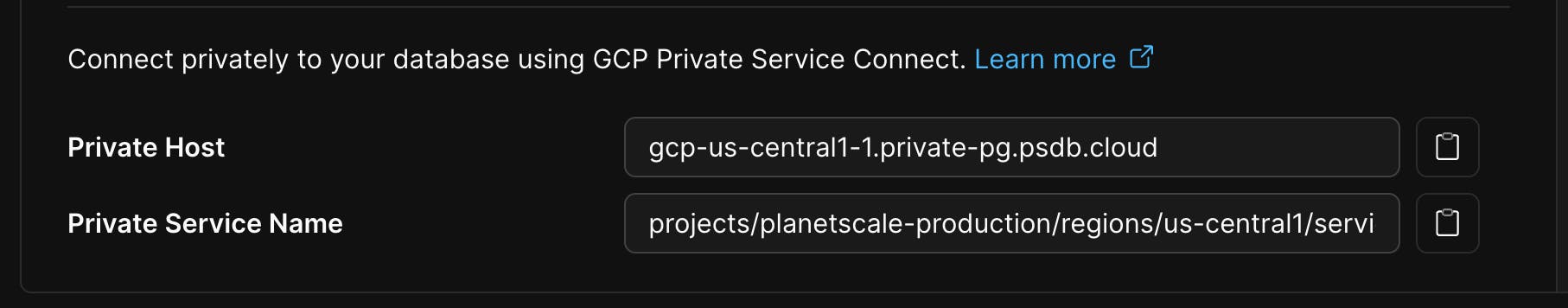
Save these two attributes for your records and the rest of the configuration.
Note
Both the
Private HostandPrivate Service Namevalues are the same for all roles for a given PlanetScale databaseBranch. Once enabled, any role can use the Private Service Connect endpoint. You do not need to configure this per PlanetScaleRole.Enable required APIs: Ensure Cloud DNS and Service Directory APIs are enabled for automatic DNS zone creation:
Via GCP Console:
- Confirm you are in the proper
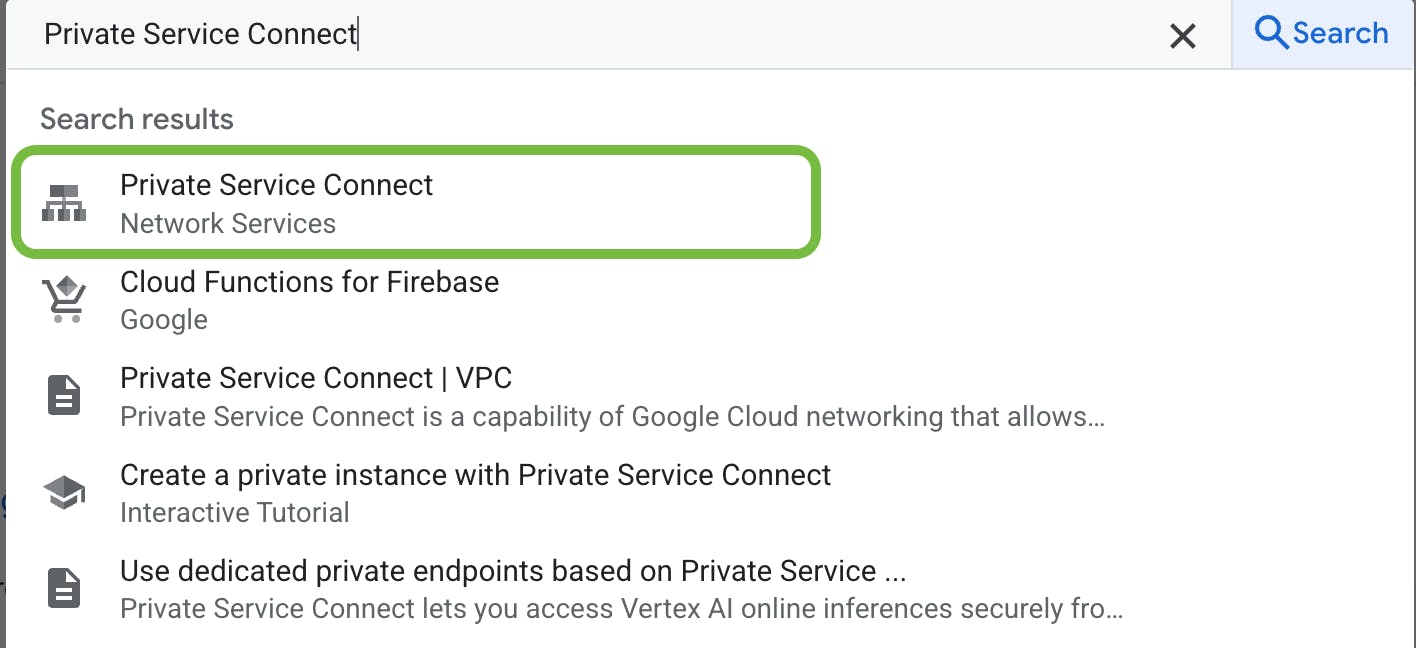
<gcp-region>from the project selector - From the top search bar, search for
CloudDNSand select it from the results - Click to enable the API
- From the top search bar, search for
Service Directoryand select it from the results - Click to enable the API
- Confirm you are in the proper
Navigate to Private Service Connect: In the GCP Console:
- Confirm you are in the proper
<gcp-region>from the project selector - From the top search bar, search for
Private Service Connectand select it from the results
- Confirm you are in the proper
Create a new endpoint: Click "+ Connect endpoint".
Configure endpoint details:
- Target: Select "Published Service"
- Target Service: Enter the
Private Service Namerecorded from the PlanetScale Dashboard - Endpoint name: Choose a descriptive name (e.g., "planetscale-main" uses the
Branchname in it. This name will be part of the connection host string you use going forward) - Network: Select your VPC network
- Subnet: Choose a subnet that your application servers can access
- Create an IP Address: Reserve a static IP address for the endpoint
- Enable Global Access: Recommended - allows applications in other regions to reach the endpoint
- Create a namespace: Recommended - Set a namespace in
Service Directoryto enable creation of an entry for this endpoint
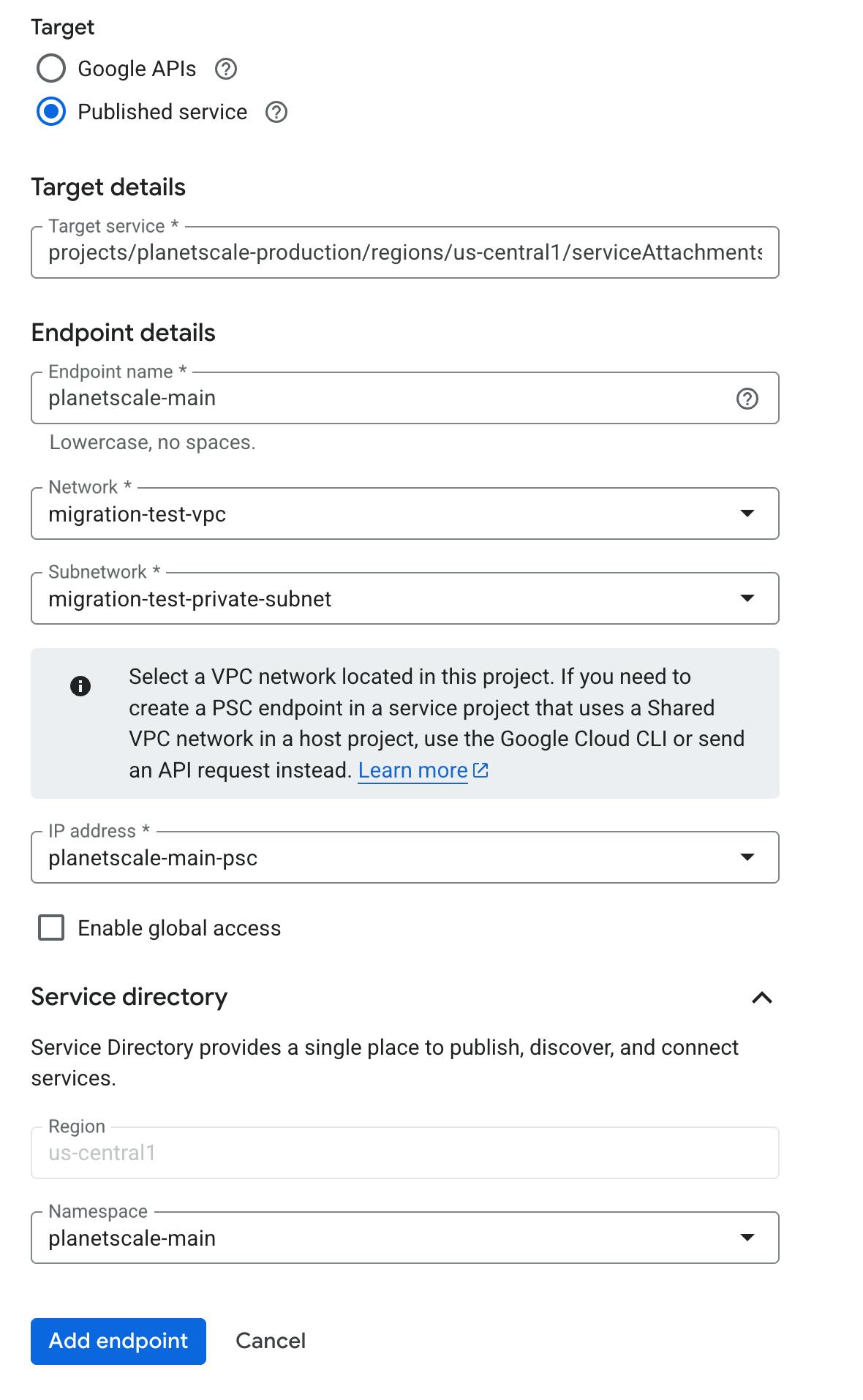
Create the endpoint: Click "Add Endpoint" and wait for the endpoint status to show "Accepted" (this may take several minutes).
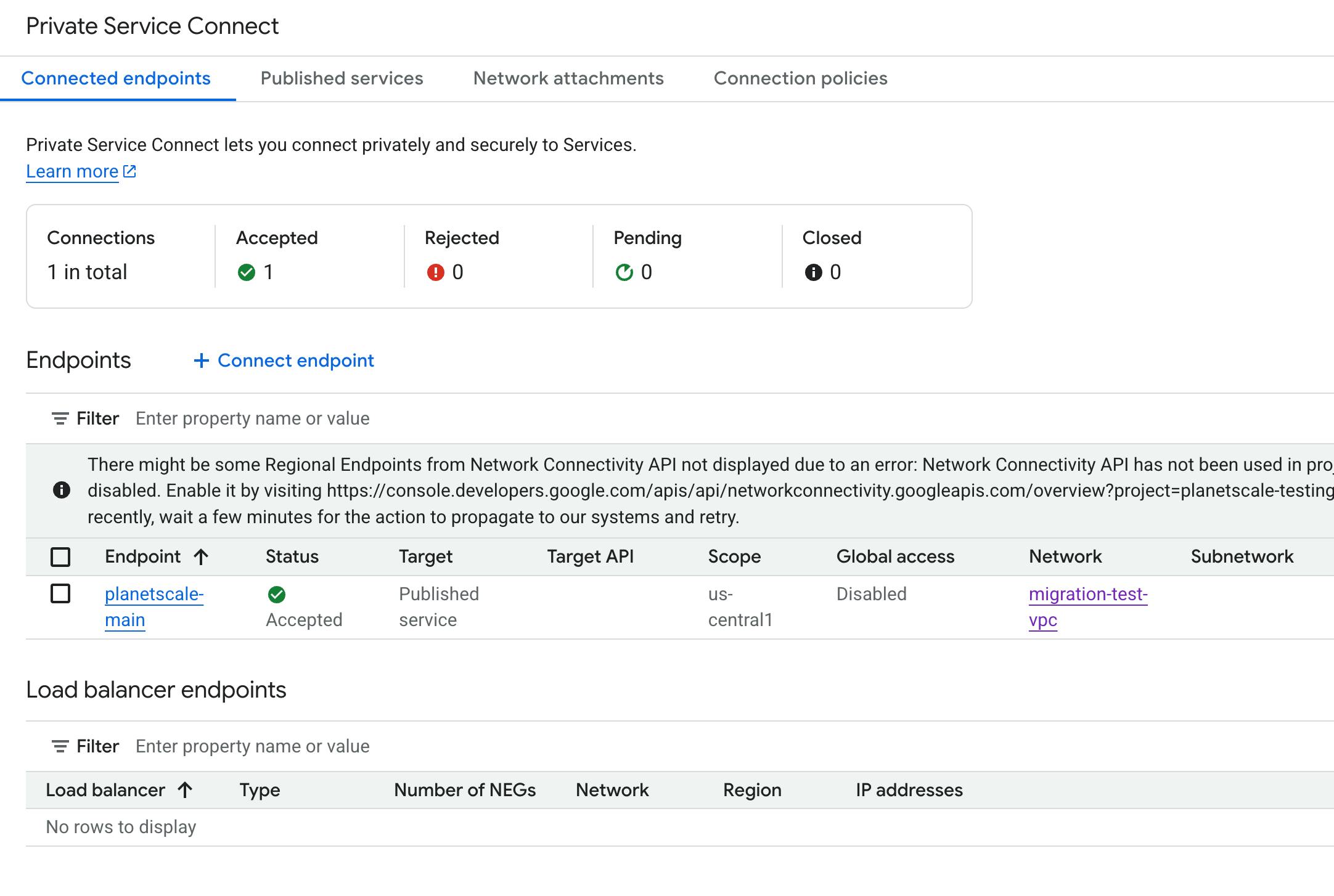
Verifying your Private Service Connect endpoint connectivity
Confirm endpoint status: In the GCP Console, verify that your endpoint's status shows "Accepted".
Test DNS resolution: If Cloud DNS is enabled, GCP automatically creates a private Cloud DNS zone for your endpoint. The DNS zone will match the
Private Host(recorded earlier from the PlanetScale Dashboard).You can verify by navigating to the
Cloud DNSpage from the left Nav: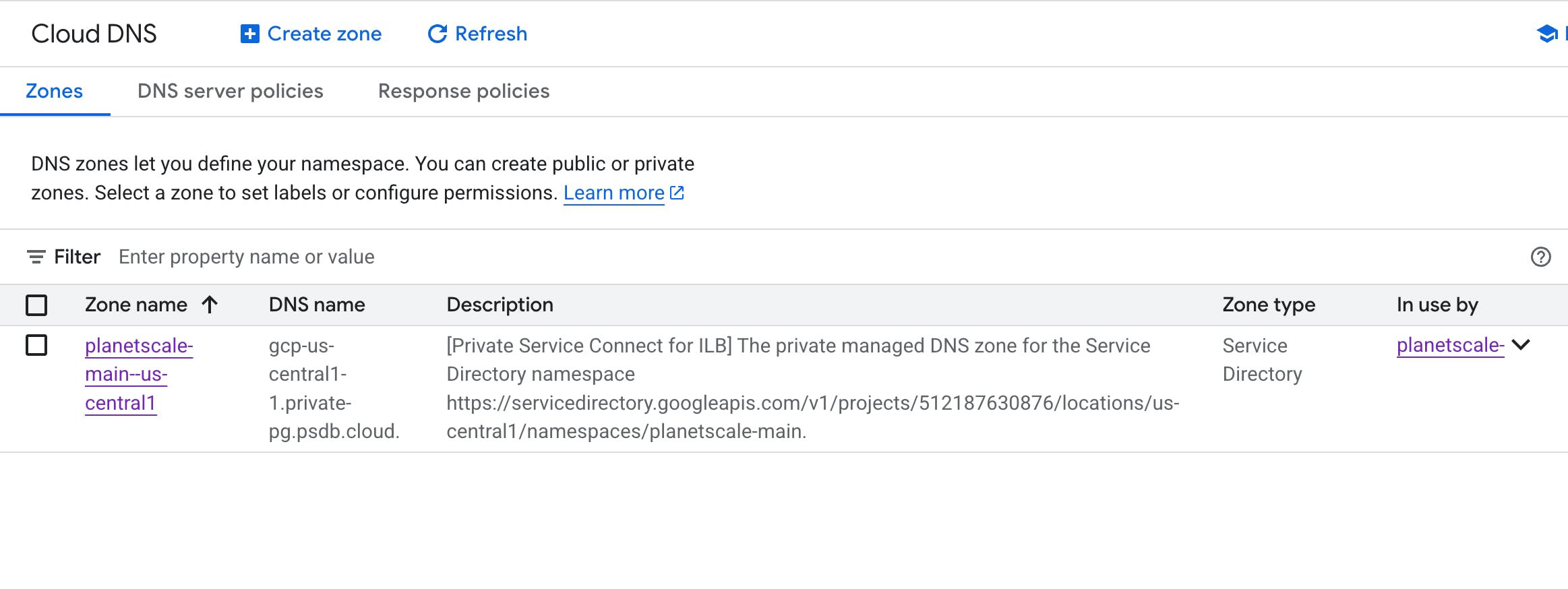
To address the actual host endpoint you will use, you need to combine the
Endpoint nameyou defined with the DNS zone name here (same as thePrivate Hostrecorded earlier).From this example:
Endpoint name= planetscale-mainPrivate Host= gcp-us-central1-1.private-pg.psdb.cloud
Which results in:
planetscale-main.gcp-us-central1-1.private-pg.psdb.cloud
To confirm DNS is working properly in your VPC, run a DNS lookup from a VM instance in your configured VPC:
dig +short planetscale-main.gcp-us-central1-1.private-pg.psdb.cloud 10.128.0.17
Test your PostgreSQL connection:
Once you have confirmed DNS resolution, test the private endpoint:
psql 'host=planetscale-main.gcp-us-central1-1.private-pg.psdb.cloud port=5432 user=postgres.XYZ234 password=pscale_pw_REDACTED dbname=postgres sslmode=require'
Update your connection strings
Once your Private Service Connect endpoint is established and verified, update your application's connection strings to use the private endpoint address. Note that you need both the Endpoint name you configured and the Private Host from the PlanetScale dashboard to form the full hostname for your application to use.
- Original:
gcp-us-central1-1.pg.psdb.cloud - Private:
planetscale-main.gcp-us-central1-1.private-pg.psdb.cloud
Replace the hostname in your connection strings while keeping all other parameters (user, password, database name, etc.) the same.
VPC considerations
Your VPC configuration should allow:
- Private Google Access: Enable this if your compute instances don't have external IP addresses
- Subnet routing: Ensure proper routing between your application subnets and the PSC endpoint subnet
- Network tags: Use network tags to organize and control access to your PSC endpoint
Troubleshooting
If you're experiencing connectivity issues:
- Verify endpoint status: Ensure your Private Service Connect endpoint shows "Accepted" status
- Test DNS resolution: Verify DNS is resolving to the private IP address in your VPC
- Check VPC routing: Ensure there are no route conflicts or missing routes
- Verify network connectivity: Use tools like
telnetorncto test port connectivity - Contact support: If issues persist, contact PlanetScale support with your endpoint configuration details
Next steps
- Learn about PostgreSQL roles and permissions
- Configure connection pooling with PgBouncer
- Monitor your connections and performance
Need help?
Get help from the PlanetScale Support team, or join our GitHub discussion board to see how others are using PlanetScale.