Overview
The following guide describes how PlanetScale Managed with GCP Private Service Connect works and how to set it up.If you are on a Scaler Pro plan and would like to set up GCP Private Service Connect endpoint, see our Private connections documentation.
How PlanetScale Managed and GCP Private Service Connect work
Private Service Connect (PSC) allows a service producer (PlanetScale) offer services to a service consumer without the consumer being a member of the service producer’s organization. The service producer is the Google Cloud project controlled by PlanetScale, and the service consumer is the project(s) where your applications operate. Your applications connect to a private IP you allocate in your project, which is routed to your PlanetScale databases in the project that PlanetScale controls. GCP PSC requires multiple components:- A Private Service Connect Service Attachment (also known as a Published Service) deployed in the project that PlanetScale controls on your behalf.
- A Private Service Connect Endpoint deployed in the project(s) that your applications operate in.
Step 1: Initiating the setup process
If you would like to initiate the process, please contact your Solutions Engineer and let them know the Google Cloud project ID(s) in which you intend to create Private Service Connect endpoints. If you need to add additional projects to the allowlist, please get in touch with your Solutions Engineer. Once they receive your project IDs and forward them to the team responsible for provisioning your deployment, the team will provide them (and ultimately you) with the Private Service Connect Service Attachment URI, which will be in the formprojects/PROJECT/regions/REGION/serviceAttachments/SERVICE_NAME.
Your Solutions Engineer will provide you the following information when the setup is complete:
Target Service(example:projects/PROJECT/regions/REGION/serviceAttachments/SERVICE_NAME)
Target Service, and you will need to configure consumer endpoints for each region.
Step 2: Establishing Private Service Connect
Refer to Google Cloud’s Access published services through endpoints document for more information on connecting to services via Private Service Connect. This document covers additional details not covered here, including the IAM roles required to perform the configuration process.Using the GCP console
The following steps are an example of establishing a Private Service Connect endpoint in the GCP Console.Obtain the Private Service Connect Attachment URI (
Target Service) from your Solutions Engineer. It will be in the format: projects/PROJECT/regions/REGION/serviceAttachments/SERVICE_NAME.Create a Private Service Connect Endpoint. In the GCP console, go to “Network Service > Private Service Connect” page, select the “Connected endpoints” tab, and select the ”+ Connect endpoint” button.
Add a Private Service Connect Endpoint with the following details: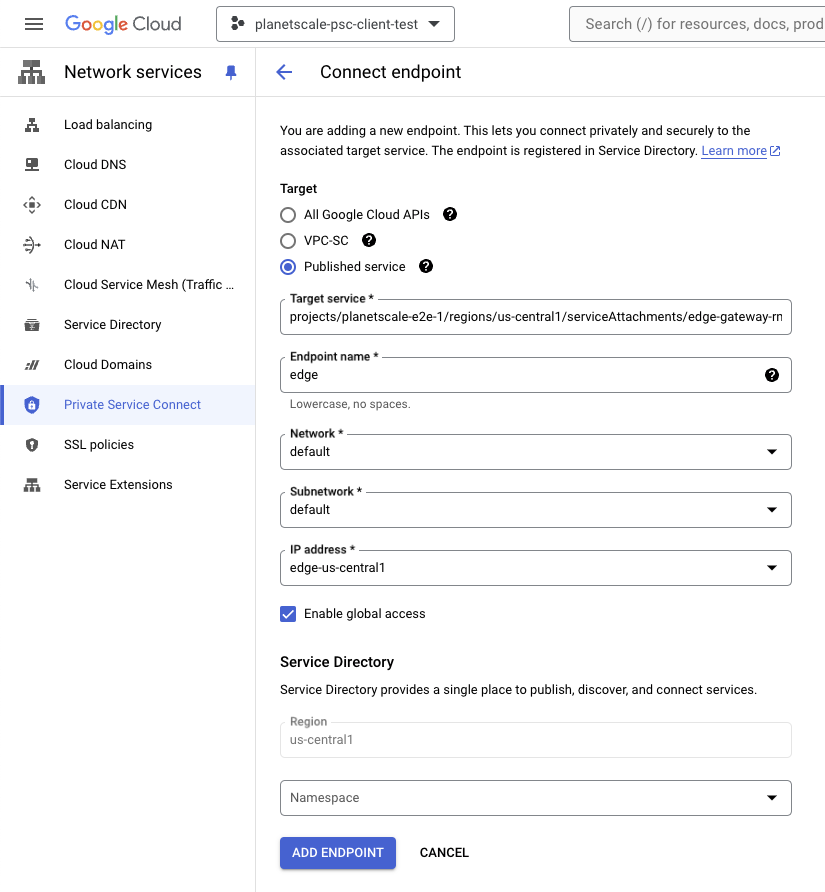
- Target: Published Service.
- Target Service: Paste the
Target Serviceattachment URI provided by your Solutions Engineer in step 1. - Name: Pick any
Endpoint Name. The examples in this document use"edge". - Network and subnet: Select the network (VPC) to create the endpoint in. The endpoint will reserve a static IP address in the subnet. The VPC and subnet must be reachable by the applications you intend to connect to your PlanetScale databases from.
- Create an IP Address: Create a reserved IP address. This is the address your applications will use to access your PlanetScale databases.
- Enable Global Access: PlanetScale recommends enabling this option. When enabled, this allows applications in other regions of your VPC to reach the PSC endpoint.

The endpoint creation process will take a minute or two. When finished, select the endpoint and verify the status is Accepted: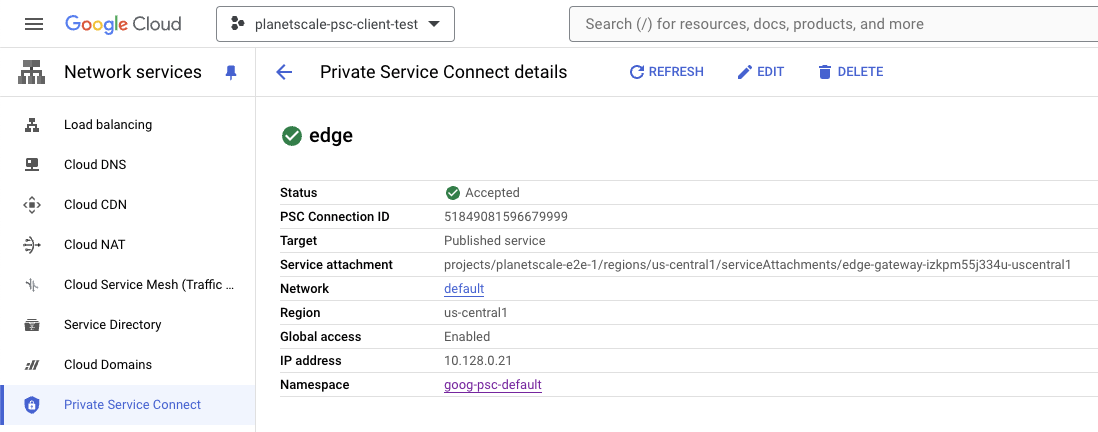

You must provide the list of projects you wish to connect from to your Solutions Engineer. Your endpoint will only function once they have been added to the allowlist in the published service.
Step 3: Verifying Connectivity
DNS
Private Service Connect services created after May 8, 2024 automatically create private Cloud DNS records in the project where the PSC consumer endpoints are created.PSC services published before May 8, 2024 may need to create a private Cloud DNS zone and configure records pointing to the PSC endpoint IP’s manually if you wish to use DNS names to connect to your PlanetScale databases.Google maintains additional documentation covering DNS and Private Service Connect here:
Network Services > Cloud DNS. If Google was able to set up automatic DNS, you will see a new private DNS zone labeled by DNS Name:
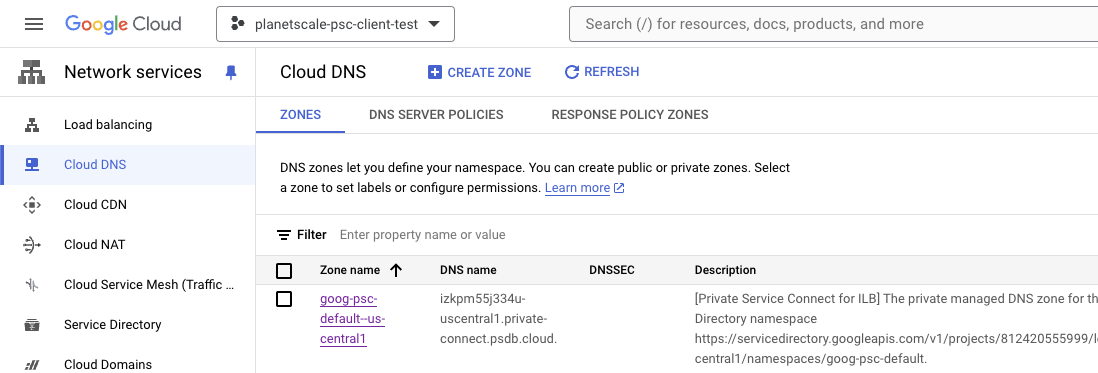
<Endpoint-Name>.<Domain-Name>
dig. In this example, the endpoint was created with the name edge and the service’s domain name was izkpm55j334u-uscentral1.private-connect.psdb.cloud:
Test connectivity
Runcurl https://<Endpoint-Name>.<Domain-Name> to verify your connectivity. A successful response will yield Welcome to PlanetScale.

